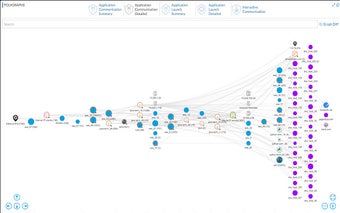
Lacework Polygraph Detects and Investigates Attacks, Cyber Attacks, and Insider Threats
By automatically analyzing massive amounts of cloud data in a continuous cycle, it’s the first solution to fully automate cloud workload security. It detects and investigates attacks and insider threats quickly and accurately and can analyze vast amounts of cloud data to determine the complete cloud kill chain.
For an application, this can result in the following insights:
The user performed a manual operation and the application is compromised. The operation is performed by a malicious actor, and the application has a compromise. The user performed an operation on the application and the user is a malicious actor. The operation is performed by a malicious actor, and the application is compromised.
Lacework Polygraph™ is based on a unique and proprietary approach that can detect and investigate breaches, cyber-attacks, and insider threats. It analyzes cloud operations at the microsecond level, helping security teams quickly and accurately identify security incidents, attacks, and insider threats. It analyzes massive amounts of data to find the full cloud kill chain, eliminating the need for rules or manual analysis.
It collects data from every cloud activity of every user, container, and process, and stores it in a single database. It can monitor changes in the database and quickly determine the event, user, role, and process that triggered it.